우선 Volatility를 다운로드 하도록 하자. 예전 버전은 Python을 이용하여 실행하였는데 최근에 2.0 으로 버전업 되면서 Python 없이 단독으로 실행이 가능해졌다.
Volatility : https://www.volatilesystems.com/default/volatility
이제 실행해 보도록 하자. 우선 예제 메모리 덤프 파일은 아래주소에서 다운로드 하도록 하자.
예제 메모리 덤프 파일 : http://www.cfreds.nist.gov/mem/memory-images.rar
우선 '-h' 옵션으로 도움말을 보도록 하자.
D:\Security Tools\Forensic\Memory Tools\volatility-2.0.standalone>volatility.exe -h
Volatile Systems Volatility Framework 2.0
Usage: Volatility - A memory forensics analysis platform.
Options:
-h, --help list all available options and their default values.
Default values may be set in the configuration file
(/etc/volatilityrc)
-d, --debug Debug volatility
--info Print information about all registered objects
--plugins=PLUGINS Additional plugin directories to use (colon separated)
--cache-directory=C:\Users\ByJJoon/.cache\volatility
Directory where cache files are stored
--no-cache Disable caching
--tz=TZ Sets the timezone for displaying timestamps
-f FILENAME, --filename=FILENAME
Filename to use when opening an image
-k KPCR, --kpcr=KPCR Specify a specific KPCR address
--output=text Output in this format (format support is module
specific)
--output-file=OUTPUT_FILE
write output in this file
-v, --verbose Verbose information
-g KDBG, --kdbg=KDBG Specify a specific KDBG virtual address
--dtb=DTB DTB Address
--cache-dtb Cache virtual to physical mappings
--use-old-as Use the legacy address spaces
-w, --write Enable write support
--profile=WinXPSP2x86
Name of the profile to load
-l LOCATION, --location=LOCATION
A URN location from which to load an address space
Supported Plugin Commands:
bioskbd Reads the keyboard buffer from Real Mode memory
connections Print list of open connections [Windows XP Only]
connscan Scan Physical memory for _TCPT_OBJECT objects (tcp connections)
crashinfo Dump crash-dump information
dlldump Dump DLLs from a process address space
dlllist Print list of loaded dlls for each process
driverscan Scan for driver objects _DRIVER_OBJECT
filescan Scan Physical memory for _FILE_OBJECT pool allocations
getsids Print the SIDs owning each process
handles Print list of open handles for each process
hashdump Dumps passwords hashes (LM/NTLM) from memory
hibinfo Dump hibernation file information
hivedump Prints out a hive
hivelist Print list of registry hives.
hivescan Scan Physical memory for _CMHIVE objects (registry hives)
imagecopy Copies a physical address space out as a raw DD image
imageinfo Identify information for the image
inspectcache Inspect the contents of a cache
kdbgscan Search for and dump potential KDBG values
kpcrscan Search for and dump potential KPCR values
lsadump Dump (decrypted) LSA secrets from the registry
memdump Dump the addressable memory for a process
memmap Print the memory map
moddump Dump a kernel driver to an executable file sample
modscan Scan Physical memory for _LDR_DATA_TABLE_ENTRY objects
modules Print list of loaded modules
mutantscan Scan for mutant objects _KMUTANT
netscan Scan a Vista, 2008 or Windows 7 image for connections and sockets
patcher Patches memory based on page scans
printkey Print a registry key, and its subkeys and values
procexedump Dump a process to an executable file sample
procmemdump Dump a process to an executable memory sample
pslist print all running processes by following the EPROCESS lists
psscan Scan Physical memory for _EPROCESS pool allocations
pstree Print process list as a tree
sockets Print list of open sockets
sockscan Scan Physical memory for _ADDRESS_OBJECT objects (tcp sockets)
ssdt Display SSDT entries
strings Match physical offsets to virtual addresses (may take a while, VERY verbose)
testsuite Run unit test suit using the Cache
thrdscan Scan physical memory for _ETHREAD objects
userassist Print userassist registry keys and information
vaddump Dumps out the vad sections to a file
vadinfo Dump the VAD info
vadtree Walk the VAD tree and display in tree format
vadwalk Walk the VAD tree
volshell Shell in the memory image
D:\Security Tools\Forensic\Memory Tools\volatility-2.0.standalone>이제 패스워드를 찾아 보도록 하자.
1) hivescan 옵션을 이용하여 스캔한다.
D:\Security Tools\Forensic\Memory Tools\volatility-2.0.standalone>volatility.exe hivescan -f xp-laptop-2005-07-04-1430.img
Volatile Systems Volatility Framework 2.0
Offset (hex)
42168328 0x02837008
42195808 0x0283db60
47598392 0x02d64b38
155764592 0x0948c770
155973608 0x094bf7e8
208587616 0x0c6ecb60
208964448 0x0c748b60
234838880 0x0dff5b60
243852936 0x0e88e688
251418760 0x0efc5888
252887048 0x0f12c008
256039736 0x0f42db38
269699936 0x10134b60
339523208 0x143cb688
346659680 0x14a99b60
377572192 0x16814b60
387192184 0x17141578
509150856 0x1e590688
521194336 0x1f10cb60
523667592 0x1f368888
527756088 0x1f74eb382) hivelist 옵션을 이용하여 리스트를 확인합니다.
D:\Security Tools\Forensic\Memory Tools\volatility-2.0.standalone>volatility.exe hivelist -f xp-laptop-2005-07-04-1430.img --profile=WinXPSP2x86
Volatile Systems Volatility Framework 2.0
Virtual Physical Name
0xe2610b60 0x14a99b60 \Device\HarddiskVolume1\Documents and Settings\Sarah\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat
0xe25f0578 0x17141578 \Device\HarddiskVolume1\Documents and Settings\Sarah\NTUSER.DAT
0xe1d33008 0x0f12c008 \Device\HarddiskVolume1\Documents and Settings\LocalService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat
0xe1c73888 0x0efc5888 \Device\HarddiskVolume1\Documents and Settings\LocalService\NTUSER.DAT
0xe1c04688 0x0e88e688 \Device\HarddiskVolume1\Documents and Settings\NetworkService\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat
0xe1b70b60 0x0dff5b60 \Device\HarddiskVolume1\Documents and Settings\NetworkService\NTUSER.DAT
0xe1658b60 0x0c748b60 \Device\HarddiskVolume1\WINDOWS\system32\config\software
0xe1a5a7e8 0x094bf7e8 \Device\HarddiskVolume1\WINDOWS\system32\config\default
0xe165cb60 0x0c6ecb60 \Device\HarddiskVolume1\WINDOWS\system32\config\SAM
0xe1a4f770 0x0948c770 \Device\HarddiskVolume1\WINDOWS\system32\config\SECURITY
0xe1559b38 0x02d64b38 [no name]
0xe1035b60 0x0283db60 \Device\HarddiskVolume1\WINDOWS\system32\config\system
0xe102e008 0x02837008 [no name]
0x8068d73c 0x0068d73c [no name]3) hashdump 옵션을 통해 hivelist에서 찾은 System 및 SAM Hive offset 값을 입력하여 확인합니다.
D:\Security Tools\Forensic\Memory Tools\volatility-2.0.standalone>volatility.exe hashdump -f xp-laptop-2005-07-04-1430.img -y 0xe1035b60 -s 0xe165cb60
Volatile Systems Volatility Framework 2.0
Administrator:500:08f3a52bdd35f179c81667e9d738c5d9:ed88cccbc08d1c18bcded317112555f4:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
HelpAssistant:1000:ddd4c9c883a8ecb2078f88d729ba2e67:e78d693bc40f92a534197dc1d3a6d34f:::
SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:8bfd47482583168a0ae5ab020e1186a9:::
phoenix:1003:07b8418e83fad948aad3b435b51404ee:53905140b80b6d8cbe1ab5953f7c1c51:::
ASPNET:1004:2b5f618079400df84f9346ce3e830467:aef73a8bb65a0f01d9470fadc55a411c:::
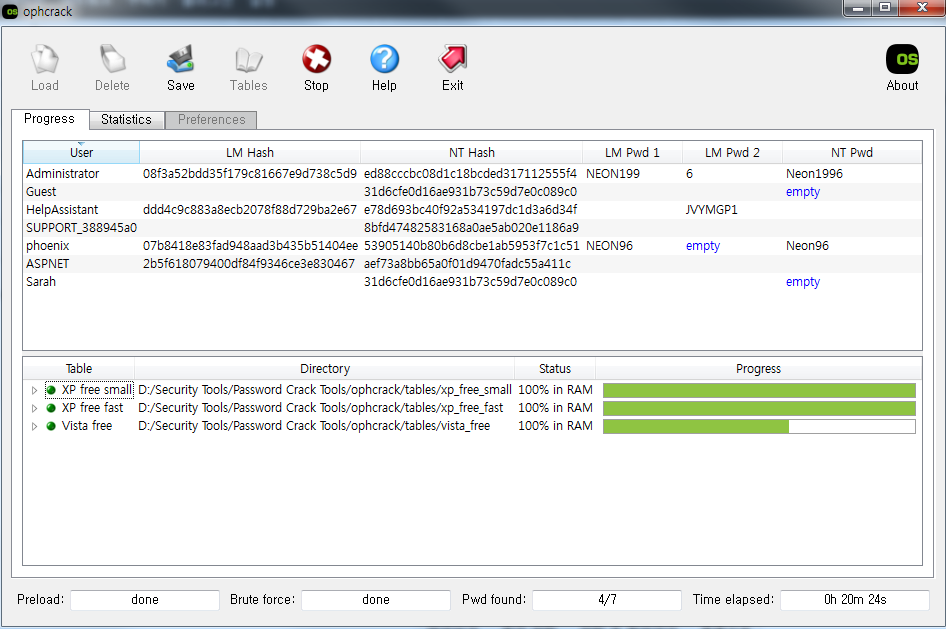
Sarah:1006:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::4) 획득한 덤프를 ophcrack이나 Cain&Abel 툴을 이용하여 크랙한다.